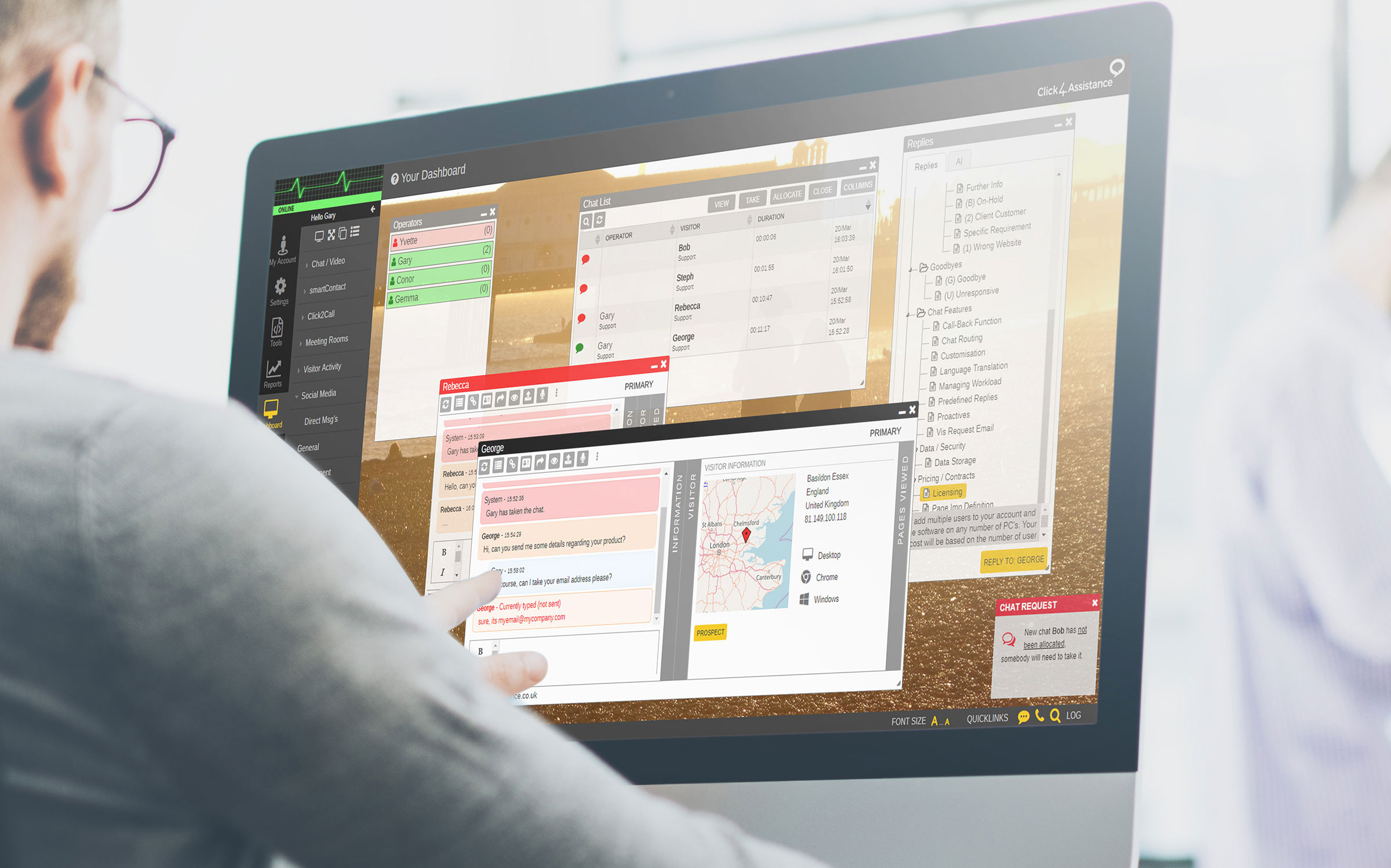
Is there Free Live Chat software?
While we don't offer free live chat software, we do provide businesses with a professional, business-class live communication system. Click4Assistance offers a free trial for you to experience our service. Free options may seem appealing, but they often come with significant limitations that can impact your professionalism and effectiveness.
Risks and limitations of free live chat software:
- Limited concurrent chats - Free chat software often restricts the number of chats that can be handled simultaneously. This limitation can lead to delays in response time and frustrate customers who must wait for assistance.
- Basic functionality - Free live communication software usually offers limited functionality compared to paid solutions. Features such as chat routing, chat history, and customisation options may be restricted or unavailable.
- Third-party ads - Many free chat software solutions display third-party ads within the chat window. These ads can distract customers, diminish the professional appearance of your website, and potentially drive traffic away from your site.
Risks of using free software for your business:
- Security vulnerabilities - Free software may not undergo rigorous security testing and updates, making it more vulnerable to cyber threats such as malware, data breaches, and hacking attempts.
- Lack of support - When the software is free it typically comes with limited or no customer support. If you encounter technical issues or need assistance, you may not have access to timely support, leading to prolonged downtime and potential loss of business.
- Scalability issues - While open-source solutions are excellent, they might struggle to keep up as your business grows, you may outgrow the capabilities of the free software, necessitating a transition to a paid solution and potential data migration challenges.
Many freeware options can only handle one conversation at a time and offer limited functionality. Using such software may compromise the professional appearance of your website and expose your customers to third-party ads.
Why not use skype?
Skype is a popular communication tool, but it's not ideal for business-class live chat. Unlike Click4Assistance, Skype requires someone from your company to be online to accept chats, and both parties need to be online simultaneously, which may not align with your customers' availability.
Why Click4Assistance is the Better Live Chat Tool:
- Availability - With Click4Assistance, you don't always need someone online to accept chats. The system can handle chats automatically, even when your team is offline.
- Convenience - Customers can leave messages when your team is unavailable, and you can respond to them later. This flexibility ensures that you never miss an opportunity to engage with your customers.
- Seamless integration - Click4Assistance seamlessly integrates with your website, providing a professional and unified chat experience for your customers.
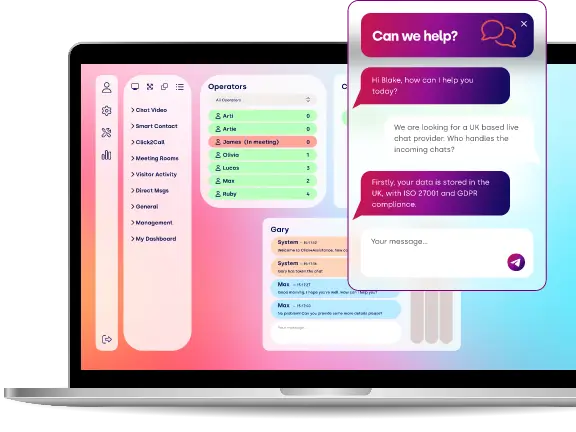
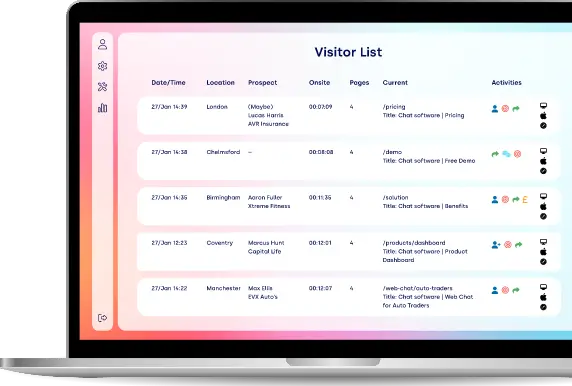
- Advanced features - Click4Assistance offers a wide range of features, including real-time visitor monitoring, chat routing, chat history, and customisable chat widgets, making it a comprehensive solution for businesses of all sizes.
- Security - Click4Assistance prioritises security, offering features like end-to-end encryption and data protection to keep your conversations and customer data secure.
Overall, Click4Assistance provides a more robust, flexible, and secure live communication solution compared to Skype, making it the better choice for businesses looking to enhance their customer service and engagement.
The alternative
Investing in professional live chat software is a sensible choice. With Click4Assistance, you get a fully customisable, feature-rich solution that integrates seamlessly with your website, costing less than £1/day.
Experience it yourself with our free trial
Sign up for our no-obligation free trial on our website and start chatting with visitors right away, without providing any payment details.
Open-Source software security risks

Licensing/IP Issues:
- Risk - Misinterpreting or violating licensing agreements can lead to legal implications.
- Likelihood - Low
- Example - Oracle filed a lawsuit against Google for copyright infringement related to Java APIs.
Unmaintained/Outdated Software:
- Risk - Vulnerabilities increase when open-source projects aren't regularly maintained.
- Likelihood - High
- Example - A critical vulnerability in the Linux kernel, StackRot, posed risks for businesses.
Publicly available source code:
- Risk - Transparency can become a weakness if attackers exploit open-source code.
- Likelihood - Moderate
- Example - Vulnerabilities within WooCommerce allowed remote users to gain control over WordPress sites.
Lack of oversight of source code for security:
- Risk - Cybercriminals can exploit vulnerabilities due to lack of oversight in open-source projects.
- Likelihood - High
- Example - Ghost script revealed a critical remote code execution vulnerability, posing a severe threat to the Linux ecosystem.
Uncertain Long-term Sustainability:
- Risk - Abandoned projects leave businesses without support, updates, and security patches.
- Likelihood - Low
- Example - Python 3.7’s official support ended, making it difficult to secure the code.
Operational issues with open-source components:
- Risk - Incompatibility, poor documentation, and insufficient support compromise security.
- Likelihood - Moderate
- Example - Microsoft researchers warned of hackers exploiting a deprecated web server, Boa, used by IoT devices.
Bad developer practices:
- Risk - Contributors indulging in bad practices increase vulnerability.
- Likelihood - Moderate
- Example - An SQL injection vulnerability was detected in MOVEit Transfer, an open-source web application.
Reducing open-source software security risks
Licensing/IP Issues
Conduct in-depth licensing reviews and ensure compliance with licensing terms.
How Click4Assistance resolves licensing and intellectual property issues:
- Click4Assistance helps overcome Licensing/IP issues by ensuring that our software complies with all licensing agreements and regulations.
- We conduct thorough reviews to ensure that our clients are fully compliant with licensing terms, helping them avoid any legal implications.
- We provide guidance and support to our clients to help them understand and adhere to licensing agreements effectively.
Unmaintained/Outdated Software
Create a regular update schedule for open-source components to track security advisories.
Click4Asistance solution to unmaintained/outdated software issues
Click4Assistance stays ahead of the curve by regularly enhancing and maintaining our live chat software, solving the problem of outdated or neglected systems. Our support team is dedicated to ensuring that our software remains up-to-date, secure, and fully functional.
Publicly available source code
Implement security best practices during the coding process and conduct regular security assessments.
Why Click4Assistance avoids using publicly available source code
Click4Assistance ensures tighter security measures by not making its source code publicly available. This means that our software is not open to unauthorised access or exploitation.
We implement stringent security best practices during the coding process and conduct regular security assessments to identify and address any vulnerabilities. This ensures that our live chat software remains secure and protected against potential cyber threats.
Bad developer practices
Bad Developer Practices encompass a range of habits and behaviours that can compromise the quality, efficiency, and security of software development.
Here are five common bad developer practices:
- Writing illegible code
- Copying and pasting code instead of refactoring
- Giving variables vague or unhelpful names
- Failing to handle exceptions properly
- Checking in untested code
Click4Assistance's comprehensive approach to secure coding practices
In addition to providing training and guidance on secure coding practices, Click4Assistance ensures that our developers are aware of and avoid other bad practices. These practices include:
- Hardcoding credentials - Developers should not hardcode sensitive information such as passwords or API keys directly into the code, as this makes it easier for attackers to access.
- Improper error handling - Inadequate error handling can lead to security vulnerabilities such as information leakage or denial of service attacks. Our developers are trained to handle errors securely to prevent such issues.
By avoiding these bad practices and following secure coding guidelines, Click4Assistance ensures that our live chat software remains secure and protected against potential threats.
Cybersecurity solutions to protect open-source software
Managed Service Providers (MSPs) can counter open-source software security risks by using cybersecurity solutions tailored to protect them, such as:
Endpoint Detection and Response (EDR) solutions
Endpoint Detection and Response (EDR) solutions are a vital component of modern cybersecurity strategies. These solutions are specifically designed to protect endpoints, which include devices such as desktops, laptops, mobile phones, and servers, from cyber threats. EDR solutions monitor endpoints in real-time to detect and respond to suspicious activities, potential security breaches, and advanced threats.
Key features of EDR solutions:
- Real-time monitoring - EDR solutions continuously monitor endpoints for any signs of malicious activity, unauthorised access, or suspicious behaviour.
- Threat detection - EDR solutions use advanced algorithms and machine learning techniques to identify known and unknown threats, including malware, ransomware, and zero-day attacks.
- Behavioural analysis - EDR solutions analyse endpoint behaviour to identify anomalies and deviations from normal patterns, helping to detect sophisticated attacks that may evade traditional security measures.
- Incident response - EDR solutions provide real-time alerts and response capabilities, allowing security teams to quickly investigate and remediate security incidents before they escalate.
- Forensic analysis - EDR solutions collect and store detailed endpoint activity data, enabling security teams to conduct forensic analysis and identify the root cause of security incidents.
- Endpoint isolation and quarantine - EDR solutions can isolate compromised endpoints from the network and quarantine malicious files or processes to prevent further spread of the attack.
- Integration with security operations centre (SOC) - EDR solutions integrate with SOC platforms, allowing security teams to correlate endpoint data with other security events and incidents for comprehensive threat detection and response.
Benefits of EDR solutions:
- Improved threat detection and response - EDR solutions provide real-time visibility into endpoint activity, allowing security teams to detect and respond to threats more effectively.
- Reduced dwell time - By detecting and responding to threats faster, EDR solutions help reduce dwell time, the time between a security breach and its detection. Which minimises the potential impact of cyber-attacks.
- Enhanced endpoint security posture - EDR strengthens the overall security posture of an organisation by providing advanced threat detection capabilities and proactive incident response.
- Compliance and reporting - This help organisations meet regulatory compliance requirements by providing detailed endpoint activity logs, audit trails, and compliance reports.
- Cost-effective security - EDR solutions offer a cost-effective way to improve endpoint security by automating threat detection and response processes, reducing the workload on security teams, and minimising the risk of data breaches and cyber-attacks.
In summary, EDR (Endpoint Detection and Response) solutions play a crucial role in safeguarding endpoints from advanced cyber threats, significantly enhancing the overall security posture of an organisation. Click4Assistance prioritises security by providing robust EDR solutions.
Our EDR solutions offer:
- Real-time threat detection
- Incident response
- Forensic analysis capabilities
This proactive approach helps organisations stay ahead of cyber threats, effectively mitigating security risks and ensuring a secure environment for their data and systems.
Security Operations Centre (SOC)
A Security Operations Centre (SOC) is a centralised unit within an organisation that is responsible for monitoring, detecting, analysing, and responding to cybersecurity incidents. It serves as the nerve centre for cybersecurity operations, providing real-time visibility into an organisation’s security posture and ensuring the confidentiality, integrity, and availability of its information assets.
Key functions of a Security Operations Centre (SOC):
- Threat Monitoring - SOC analysts continuously monitor network traffic, system logs, and security alerts to identify potential security threats and suspicious activities.
- Incident Detection - Using advanced security tools and technologies, SOC analysts detect and analyse security incidents, including cyber-attacks, data breaches, malware infections, and insider threats.
- Alert Triage and Investigation - Analysts assess and prioritise security alerts, conduct investigations into potential security incidents, and evaluate the scope, severity, and impact of the threats.
- Threat Intelligence - It aids in collecting and analysing threat intelligence data from diverse sources to remain updated on the latest cyber threats, attack methods, and vulnerabilities.
- Incident Response - Operation analysts respond to security incidents by containing, mitigating, and remediating the threats, minimising the damage, and restoring the affected systems and data to normal operation.
- Forensic Analysis - Security Operations Centre (SOC) analysts perform forensic analysis of security incidents to determine the origin, root cause, and impact of threats, collecting evidence for investigative and legal purposes.
- Vulnerability Management - It is designed to perform vulnerability assessments, patch management, and security configuration audits to identify and remediate security weaknesses and reduce the organisation’s attack surface.
- Security Compliance - Analysts ensure that the organisation’s security controls, policies, and procedures comply with regulatory requirements, industry standards, and best practices.
Components of a Security Operations Centre (SOC):
- Security Information and Event Management (SIEM) System - A SIEM system collects, correlates, and analyses security event data from various sources, including network devices, servers, applications, and security tools.
- Threat Intelligence Platform (TIP) - A TIP aggregates, enriches, and analyses threat intelligence data from external sources to identify emerging threats and trends.
- Security Analytics Tools - Security analytics tools use advanced analytics, machine learning, and artificial intelligence (AI) techniques to detect and analyse security threats and anomalous activities.
- Incident Response Platform (IRP) - An IRP provides workflow automation, case management, and collaboration capabilities to streamline the incident response process.
- Forensic Investigation Tools - Forensic investigation tools help SOC analysts collect, preserve, and analyse digital evidence from security incidents for investigation and legal purposes.
Benefits of a Security Operations Centre (SOC):
- Improved Threat Detection and Response - SOC provides real-time monitoring, analysis, and response to security incidents, reducing the time to detect and respond to threats.
- Enhanced Incident Response Capabilities - It also helps organisations quickly identify, contain, and mitigate security incidents, minimising the impact and damage caused by cyber-attacks.
- Better Security Posture - A Security Operations Centre (SOC) strengthens the overall security posture of an organisation by proactively identifying and mitigating security risks and vulnerabilities.
- Regulatory Compliance - It also assists organisations in meeting regulatory compliance requirements by implementing and enforcing security controls, policies, and procedures.
- Cost-Effective Security - A SOC helps organisations reduce the risk of data breaches, financial losses, and reputational damage by preventing and mitigating security incidents effectively.
In summary, a Security Operations Centre (SOC) is a critical component of an organisation’s cybersecurity strategy, providing centralised monitoring, detection, analysis, and response to security incidents. By leveraging advanced security tools, technologies, and processes, a SOC helps organisations stay ahead of cyber threats and protect their information assets effectively.
Security Information and Event Management (SIEM) solutions
Despite the risks, some clients may prefer open-source platforms. Your Managed Service Provider (MSP) can ensure protection and oversight by implementing reliable cybersecurity solutions, although this may require significant time and effort.
ConnectWise offers a comprehensive suite of cybersecurity management solutions, including Endpoint Detection and Response (EDR) with 24/7 Security Operations Centre (SOC) support. Alternatively, you can access our full package, which includes robust security features, eliminating the need for separate SIEM solutions.
Integrating live chat with updated security features is simple and can be done in less than 5 steps.
Register for a Free demo to learn more about how Click4Assistance provides the best all-round Live Chat Software solution for your business.